Cybersecurity Tech Brief By HackerNoon
Learn the latest Cybersecurity updates in the tech world.
- Update frequency
- every day
- Average duration
- 8 minutes
- Episodes
- 204
- Years Active
- 2023 - 2024

SCIM: A Critical Yet Underappreciated Element in Enterprise IAM
This story was originally published on HackerNoon at: https://hackernoon.com/scim-a-critical-yet-underappreciated-element-in-enterprise-iam.
Discover how SCIM improves enterprise IAM com…
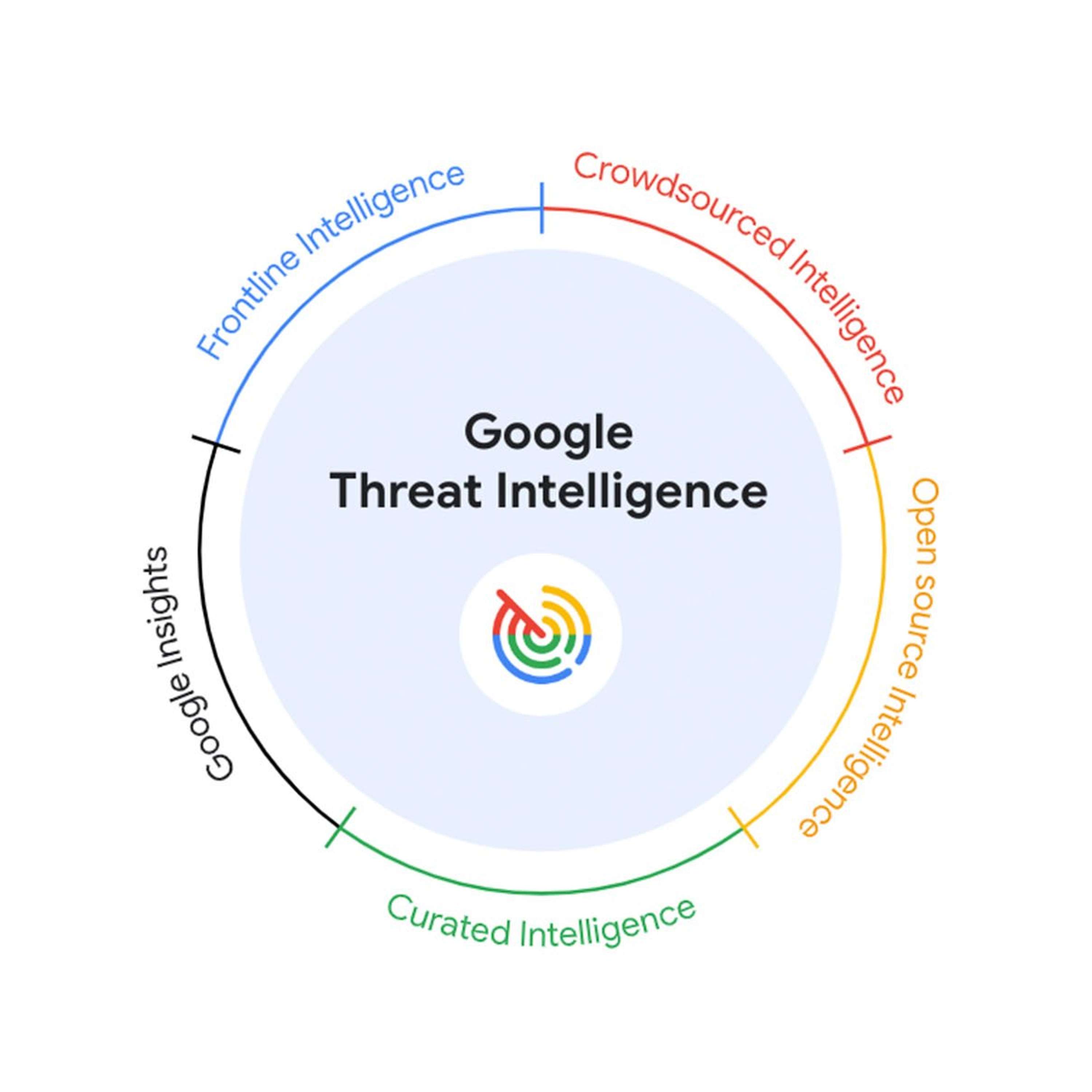
Actionable Threat Intelligence at Google Scale: Meet Google Threat Intelligence Powered by Gemini
This story was originally published on HackerNoon at: https://hackernoon.com/actionable-threat-intelligence-at-google-scale-meet-google-threat-intelligence-powered-by-gemini.
Google Thre…
The Snowflake Hack and Its Domino Effect
This story was originally published on HackerNoon at: https://hackernoon.com/the-snowflake-hack-and-its-domino-effect.
Learn how to secure your company's data in the wake of major breach…

Tech Expert Durga Sanagana Advances Next-Gen Firewalls and Threat Modeling Techniques
This story was originally published on HackerNoon at: https://hackernoon.com/tech-expert-durga-sanagana-advances-next-gen-firewalls-and-threat-modeling-techniques.
Durga Prasada Rao Sana…

Critical Vulnerability in Swedish BankID Exposes User Data
This story was originally published on HackerNoon at: https://hackernoon.com/critical-vulnerability-in-swedish-bankid-exposes-user-data.
A common misconfiguration found in services integ…

Secure and Dynamic Publish/Subscribe: LCMsec: Related Work
This story was originally published on HackerNoon at: https://hackernoon.com/secure-and-dynamic-publishsubscribe-lcmsec-related-work.
Introducing LCMSec, a secure, brokerless Publish/Sub…

Secure and Dynamic Publish/Subscribe: LCMsec: Description of LCM
This story was originally published on HackerNoon at: https://hackernoon.com/secure-and-dynamic-publishsubscribe-lcmsec-description-of-lcm.
Introducing LCMSec, a secure, brokerless Publi…

Cybersecurity and AI: Meetings and Insights from the Nexus 2050 Conference
This story was originally published on HackerNoon at: https://hackernoon.com/cybersecurity-and-ai-meetings-and-insights-from-the-nexus-2050-conference.
The Nexus 2050 conference brought …

Understanding Authentication: A Guide to Cookie-Based and Session-Based Authentication
This story was originally published on HackerNoon at: https://hackernoon.com/understanding-authentication-a-guide-to-cookie-based-and-session-based-authentication.
Cookies-Based Authenti…

Cyber Scum Are Free To Exploit Vulnerabilities Without Fear
This story was originally published on HackerNoon at: https://hackernoon.com/cyber-scum-are-free-to-exploit-vulnerabilities-without-fear.
Cyber Scum Are Free To Exploit Vulnerabilities W…

Effective Proxy Server Design and Implementation
This story was originally published on HackerNoon at: https://hackernoon.com/effective-proxy-server-design-and-implementation.
Explore the principles of proxy server design, key architec…

Balancing Usability and Security in the Wake of a Breach: An Interview With Magpie Protocol's CIO
This story was originally published on HackerNoon at: https://hackernoon.com/balancing-usability-and-security-in-the-wake-of-a-breach-an-interview-with-magpie-protocols-cio.
We sat with …

Solving Crimes with Data: The BTK Killer and the Power of Metadata Analysis
This story was originally published on HackerNoon at: https://hackernoon.com/solving-crimes-with-data-the-btk-killer-and-the-power-of-metadata-analysis.
Explore how metadata analysis led…

What is CHECK Penetration Testing and Why Do You Need It?
This story was originally published on HackerNoon at: https://hackernoon.com/what-is-check-penetration-testing-and-why-do-you-need-it.
What is CHECK Penetration Testing and Why do you ne…

Understanding IP Geolocation: Its Benefits and Challenges
This story was originally published on HackerNoon at: https://hackernoon.com/understanding-ip-geolocation-its-benefits-and-challenges.
Explore how IP geolocation shapes user experience, …

A Deep Dive into Path Traversal Vulnerabilities
This story was originally published on HackerNoon at: https://hackernoon.com/a-deep-dive-into-path-traversal-vulnerabilities.
Discover how path traversal attacks work and learn effective…

Can Your Java Cryptography Architecture Survive a Quantum Attack?
This story was originally published on HackerNoon at: https://hackernoon.com/can-your-java-cryptography-architecture-survive-a-quantum-attack.
Learn how to optimize Java Cryptography Arc…

Infinidat Revolutionizes Enterprise Cyber Storage Protection, Combats Ransomware And Malware Threats
This story was originally published on HackerNoon at: https://hackernoon.com/infinidat-revolutionizes-enterprise-cyber-storage-protection-combats-ransomware-and-malware-threats.
Sophisti…

FireTail Unveils Free Access For All To Cutting-Edge API Security Platform
This story was originally published on HackerNoon at: https://hackernoon.com/firetail-unveils-free-access-for-all-to-cutting-edge-api-security-platform.
This initiative opens the door fo…

The Role of Data Destruction in Cybersecurity
This story was originally published on HackerNoon at: https://hackernoon.com/the-role-of-data-destruction-in-cybersecurity.
What happens to information when it's no longer necessary? If …